Securing Your Email with DKIM + What You Need to Know
As email becomes an increasingly important communication factor, organizations must understand how DKIM works and take steps to properly configure it for their needs to remain compliant with mailbox providers and protect their reputation.
Email authentication technology like DKIM will help protect your organization and customers from phishing, spam, and other email-based threats. In this article, you’ll find a comprehensive overview of DKIM and its benefits and steps to add DKIM authentication to your system.
What is DKIM?
DKIM (Domain Keys Identified Mail) is a widely used email authentication method that adds a digital signature to outgoing messages. The receiving mail servers that get messages signed with DKIM can verify the sender’s identity and ensure that those messages have come from the sender, not someone impersonating the sender.
Compared with the most frequently used SMTP (Simple Mail Transfer Protocol), DKIM adds another layer of protection because it includes a way to verify the sender before delivering an email. DKIM is also superior to SPF because it survives forwarding, protecting message integrity.
How Does DKIM Work?
DKIM works by cryptographically signing email messages with a key unique to your organization stored in a public repository called the DNS. When an email is sent from your domain, the receiving server will use this key to authenticate the message. This helps to ensure that the message came from a trusted source (typically your organization) and has not been spoofed or tampered with. If a message fails authentication, it can be rejected or sent to an inbox, where it will likely be flagged as suspicious or spam.
Additionally, many mailbox providers, like Gmail and Microsoft, view DKIM authentication as a positive signal when making delivery decisions. This means that having DKIM configured on your domain helps protect it from spoofing, phishing, and other malicious activity and may also result in improved inbox placement rates.
How DKIM authentication works
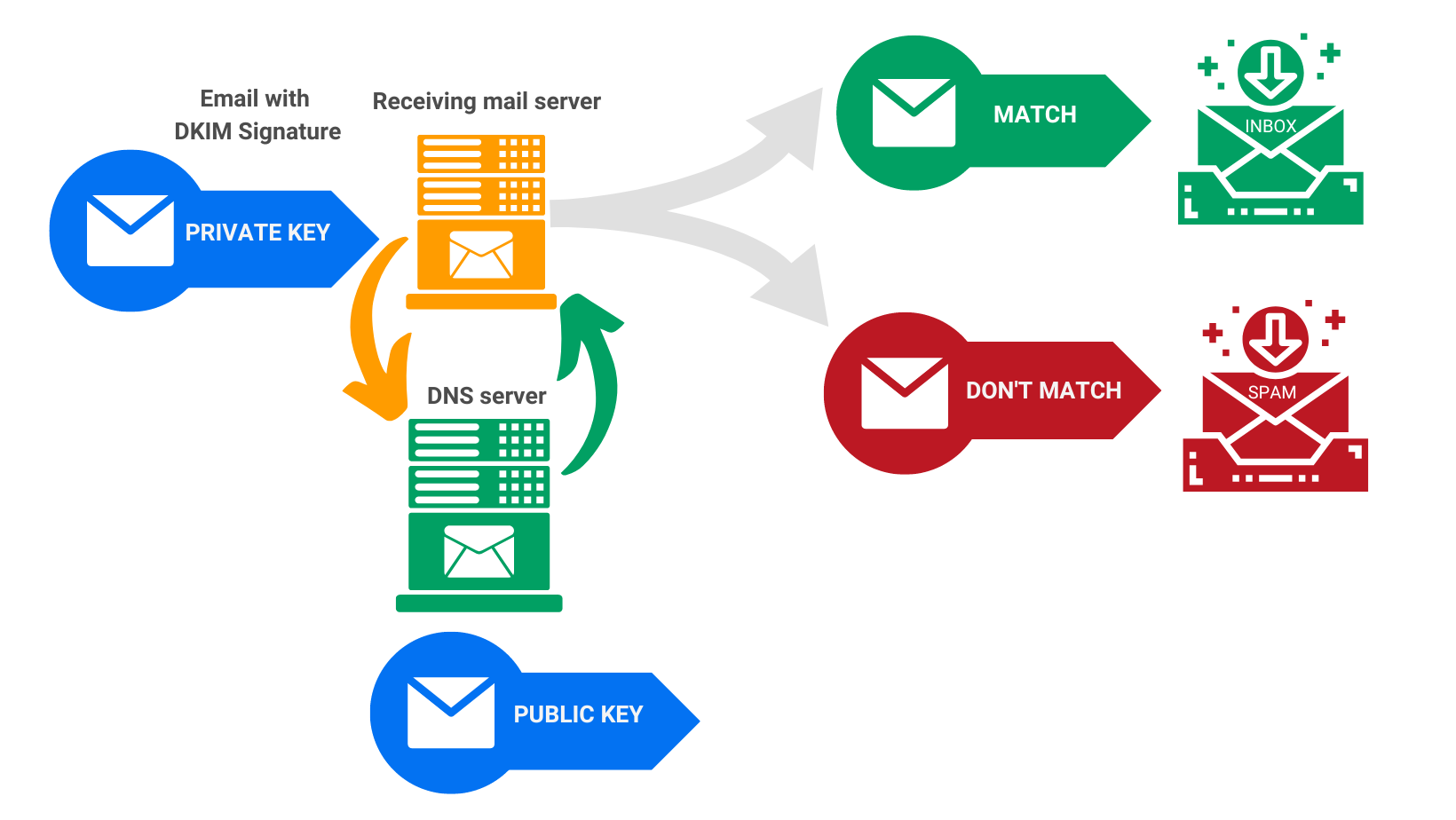
What are DKIM signatures?
A DKIM signature is a header added to emails containing specific values that allow receiving email servers to validate the message’s source.
DKIM signatures are generated with the help of two encrypted keys, one public and one private. The public key is stored in the DNS records, while the private key, included in the email header, is kept secret and should be unique to the sender. The private key is used to verify the signature when an email is signed.
How to implement DKIM on your system
To set up DKIM, your organization must use a pair of unique encrypted keys:
- a public key – included in the digital signature and accessible by internet service providers
- a private key – kept on the outgoing server and used for verifying the signature once the email is delivered
When these keys match, the sender’s identity is valid.
The public key is stored in the DNS, while the private one is kept within your organization’s mail server. When an outbound message is sent, the server will use this key to create a unique cryptographic signature attached to the message header. As it passes through other mail servers, they will reference the public DNS record and verify that the signature attached to the message matches up with what’s stored in the DNS. If it does, it can assume that the message originated from a trusted source and proceeded unaltered – otherwise, it may be rejected or flagged as spam.
Once you have generated the DKIM key and uploaded it to the DNS, you can begin monitoring messages through your mail server to ensure they are correctly signed. Incoming mail servers can detect whether a message was successfully signed by checking the cryptographic signature attached to its header. If it is missing or has been altered, the message will fail authentication and probably be marked as suspicious or delivered to an inbox with a lower score.
Here are three main reasons in support of adding DKIM authentication:
- Protect message integrity. Email content can be verified that it hasn’t been changed while being sent.
- Increase domain reputation.
- Improve email deliverability to hit more inboxes.
How to add a DKIM signature to email notifications sent through 123FormBuilder
First things first, for DKIM (Domain Keys Identified Mail) to work:
- You need to have an Enterprise account and purchase the DKIM add-on; if you are interested in this, get in touch with our sales team;
- Custom email domains used as sender or from emails need to have properly configured SPF records;
- A new TXT record needs to be created in your organization’s DNS;
- The setup needs to be validated on our side after the DNS is updated …read more.
At first glance, this might seem complicated but don’t worry; our team will guide you through the process.
There has been much activity across the email industry around DKIM recently, and organizations must stay up-to-date with the latest standards.
Mailbox providers constantly adapt their requirements, and your organization must follow suit to maintain its email reputation. Additionally, organizations should continually verify the accuracy of their DKIM keys to ensure that they are correctly configured and provide an optimal level of security.
Take steps to set up, monitor, and verify your DKIM key regularly. You can rest assured that your email messages will be authenticated and reach their intended recipients safely.

